Windows Port Scanner Utility
When troubleshooting client or server side application network connectivity issues, it is often necessary to determine if access to a certain port that the application uses is being blocked. In this article we’ll take a quick look at how to view open ports using a number of lightweight freeware tools for Microsoft Windows. You might just be surprised at how effective these free utilities are at helping you to scan open ports and get to the root of the problem.
The first tool of note is one many admin and support folk might have heard of; the Windows command line utility called netstat.exe. Netstat.exe, located in the Windows ‘System32’ folder, allows you to view ports that are open or in use on a particular host, but should not be confused with a network port scanner which actually probes a host for open ports.
To view which ports are listening (open) on a local host using netstat, from the command prompt type the following:
netstat –an ¦find /i “listening”
The results will be displayed across four columns – the protocol type, local IP address and associated port number, foreign IP address, and state – as shown in the image below. The column of interest in this case would be the second column.
By using the ‘o’ parameter as part of the netstat command, a fifth column will be displayed as part of the results. This column shows the application process ID (PID) associated with each open port. The full command would be as follows:
netstat –ano ¦find /i “listening”
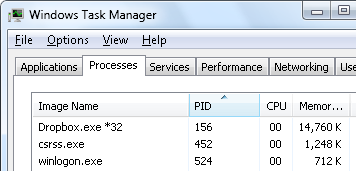
The PID information can be used to find which application is using the open port. For example, the image above shows PID 156 being associated with port 17500. By using Windows Task Manager (CTRL + SHIFT + ESC), we can see that PID 156 belongs to the application called Dropbox.exe.
The same thing can be done using tasklist.exe from the command prompt which is essentially the command line equivalent of the Windows Task Manager that will display the same information. Again, the column of interest in the results for tasklist.exe would be column two which shows the PID for each running application. Using both versions you can display other information such as the user account that the application is running under.
For a full list of parameters and further information, type “netstat /?” or “tasklist /?” in a command prompt.
Similar to netstat.exe is TCPView.exe which offers a more detailed representation of netstat.exe information in a graphical user interface (GUI). TCPView.exe is available for download from the Microsoft SysInternals website and runs as a standalone application that does not require installation. Using TCPView, not only can you scan open ports but you can also view local and remote TCP connection information such as packets sent and received, the protocol being used, as well as the initiating process.
Another interesting tool is PortQry.exe. PortQry.exe is available for download from the Microsoft Download Center and runs as a standalone command line application. (Download Link)
PortQry.exe allows you to scan open ports on a local or remote host. Once you have downloaded and extracted portqry.exe to your machine, open a command prompt, and type portqry.exe followed by a given parameter from the folder that contains the executable.
For example, typing “portqry.exe –local” will show TCP/UDP port usage for the local host. The information shown when using this parameter is similar to that of netstat.exe, however it also shows port statistics such as the number of port mappings and the number of ports in each state.
To view the TCP/UDP open port state of a remote host, type “portqry.exe –n [hostname/IP]” where [hostname/IP] is replaced with the hostname or IP address of the remote host. You can also specify to scan for a particular port using the “-e [port_number]” parameter, a particular range of ports using the “-r [start_range:end_range]” parameter, or a group of ports in a particular order using the “-o [port1, port2, port3]” parameter.
The image below shows portqry.exe being using to scan for “listening” ports on a remote host with an IP address of 192.168.0.7 and a port range of 150-160.
For a full list of parameters and further information, type “portqry.exe /?”.
This article has shown you how to scan open ports using a series of freeware utilities. These utilities will come in handy as part of troubleshooting network connectivity issues, forming part of your network auditing toolkit or contributing towards your vulnerability checks.
The ability to scan open ports using such utilities is a great thing to have. It can be useful to troubleshoot network issues and is also a critical aspect of the overall network security scanning strategy.




Comments