Security Updates for Flash Player V- 20.0.0.267
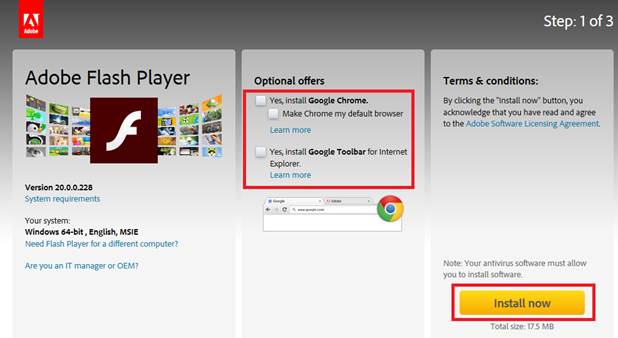
Adobe has released security updates to address multiple vulnerabilities in Flash Player. Exploitation of some of these vulnerabilities may allow a remote attacker to take control of an affected system. For securing your pc/laptop it must be updated to its latest version - 20.0.0.267 . In order to do this please follow the below instructions (Please note that in Chrome browser, the plugin is updated automatically): 1. please enter the following link: Adobe Flash Playerdownload . 2. Remove the V from the optional offers checkboxes 3. Click on the "Install now" button 4. Save the installation file. 5. Open your download folder and locate the Adobe Flash Player installer file. Then double-click on the installer to complete the installation. 6. Choose " Notify me to install updates "...