The Rapid Spanning Tree Protocol (RSTP) is an optimized version of STP. RSTP allows a newly elected root port or designated port to enter the forwarding state much quicker under certain conditions than in STP, hence quicker network convergence.
Although RSTP allows quicker network convergence, it has the same drawback as STP does: All bridges within a LAN share the same spanning tree, so redundant links cannot be blocked based on VLAN and the packets of all VLANs are forwarded along the same spanning tree.
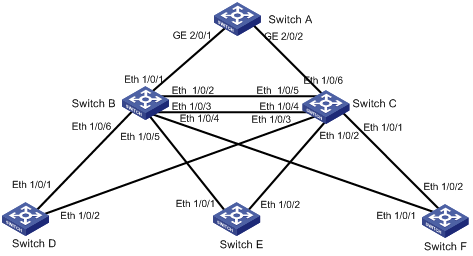
Network Diagram
Figure 1 Network diagram for RSTP configuration
Networking and Configuration Requirements
1) Switch A at the core layer.
Configure it as the root bridge.
2) Switch B and Switch C at the distribution layer.
l Configure Switch C as the standby switch of Switch B. When Switch B fails, Switch C automatically takes over to forward data.
l Configure two links between Switch C and Switch B, ensuring one link is available when the other fails.
3) Switch D, Switch E, and Switch F at the access layer.
l User PCs are connected to Switch D, Switch E, and Switch F.
l Connect Switch D, Switch E, Switch F to Switch C and Switch B.
Only RSTP-related configurations are provided in the sample configuration. In addition, as the RSTP configurations on Switch D through Switch F are basically the same, only those on Switch D are provided.
Comments