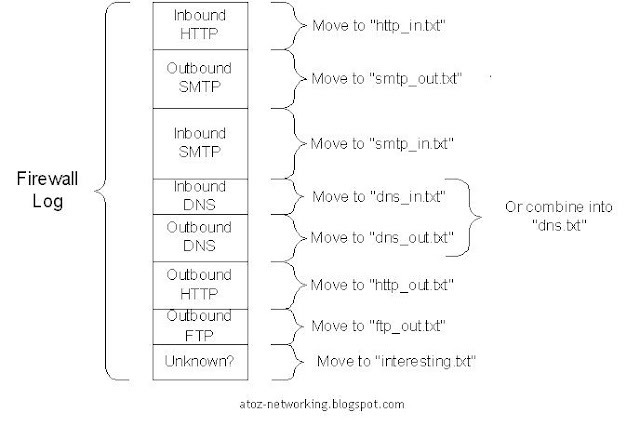
Link Aggregation

Link Aggregation Introduction Link aggregation aggregates multiple physical Ethernet ports into one logical link, also called an aggregation group. It allows you to increase bandwidth by distributing traffic across the member ports in the aggregation group. In addition, it provides reliable connectivity because these member ports can dynamically back up each other. Network Diagram Figure 1-1 Network diagram for link aggregation configuration Networking and Configuration Requirements Switch A aggregates ports GigabitEthernet 1/0/1 through GigabitEthernet 1/0/3 to form one link connected to Switch B and performs load sharing among these ports.